worried about black hat hackers? This post will show you how you How to Protect Yourself from Black Hat Hackers. People who frequently played about with computers were once referred to as “hackers” or “hackers.” The phrase is now more commonly used to describe computer professionals who hunt for ways to break into computer networks or systems. White Hat hackers purport to act in the interests of society.
How to Protect Yourself from Black Hat Hackers
When they discover a means to break into a system, they notify the business or software manufacturer so that the flaw can be repaired. Black Hat hackers are driven by a variety of reasons, some of which are not as altruistic as those of other hackers.
1.Black Hat Hackers

Black Hat hackers attempt to get access to computer networks and systems in order to carry out malicious deeds. They might want to compromise your company’s information or take down your servers.
Their motivations differ; some do it for the rush of avoiding detection, while others do it for financial gain. Some Black Hat hackers work for organised crime groups and receive generous pay for their illegal operations.
Black Hat hackers pose a major risk to your company’s information assets, whether their objective is merely to break into your system or to take your client list.
2.Firewalls
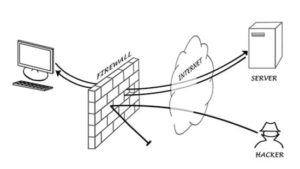
Firewalls guard the outside of the Internet connection for your business. Depending on the protocol, source address, or destination address of the packet, you can set a firewall to drop particular packets.
While other tools only examine the surface parameters and act, stateful tools function at a much deeper level of packet inspection, enhancing network security. In either case, if you want to protect your network, your business needs a firewall.
3.Content Filter

For your internal staff, content filters act as gatekeepers. You can set up a content filter to block access to specific websites or groups of websites.
For instance, you might indicate that a category of websites be prohibited if you wish to prevent employees from accessing online casinos. This is crucial since many Black Hat hackers enter your network through the websites your employees frequent.
The hacker may be able to download malware to a computer simply by viewing the site, opening the door for further actions.
4.Intrusion Prevention Systems

Intrusion Prevention Systems (IPSs) identify possible network or server intrusions and respond with a predetermined action to thwart the attack. A network’s Internet connection or a specific server may be shut down if an IPS identifies an assault that is already underway there.
An IPS may occasionally provide a false positive, but that is far preferable than an undiscovered security vulnerability on a crucial server.
5.Server Hardening

Vulnerable services that are superfluous for the operation of many servers may be running on such devices. The infamously unsafe file transfer protocol (FTP) may be used by a mail server.
Telnet is a service that some Web servers offer that is less secure than FTP. Disable extraneous services on your servers, leaving just those that are critical for their operation. This eliminates numerous entry points for hackers into your systems.
6.Computer Use Policy

Computer policies are the guidelines for using business computers and networks that you want your staff to follow.
The regulations that you specify in your company’s computer usage policy are merely put into practise by firewalls, intrusion prevention systems, and content filters. Sections on using computers, the Internet, and email should all be included in a policy. So that nobody is startled, it should also clearly state what happens if the policy is broken.
7.Security Testing

If no one has broken in that you are aware of, your network and systems will appear secure. There may have been a breach even though it doesn’t appear to be there.
To discover what vulnerabilities exist on your network, you might think about hiring a security firm to perform a penetration test. With such a list in hand, you can start to close gaps you were unaware of.
8.Employee Training

Inform your staff of the risks associated with reckless use of email, computers, and the Internet. Many people might not be aware that downloading music files onto a work computer poses a security concern.
Additionally, you want to inform them about the company’s computer usage guidelines and make sure they are aware of the potential repercussions of breaking them. A team of attentive employees is one of the finest defences against a security compromise.

